ISA is the author of the ISA/IEC 62443 Industrial Automation and Control Systems Security series of standards, the worlds only consensus-based cybersecurity standards for automation and control system applications.
IT security standards - Wikipedia Cyber Security Top 32 Cyber Security Standards - DataFlair Cyber Security Guidelines. Cyber security compliances are programs that protect the confidentiality of information and data assets. NERC Reliability Standards define the reliability requirements for planning and operating the North American bulk power system and are developed using a results-based approach that focuses on performance, risk management, and entity capabilities.
5 Critical Cybersecurity Compliance Requirements in 2022 This standard mandates organizations to have a defined plan of response in the event of a breach in critical cyber infrastructure.
Cyber Security Standards - javatpoint As a rule, the cybersecurity standards have a world-class benchmark for consistency.
 Standards
Standards Grade 7 salary.
CISAs Role in Cybersecurity.
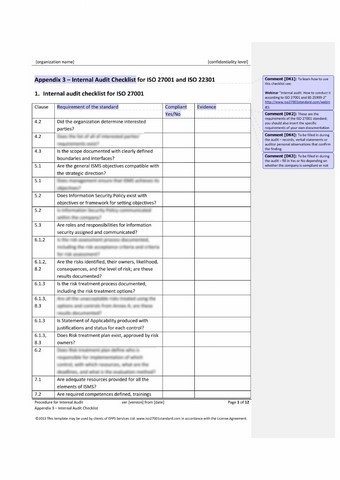
Essential Eight - Australian Signals Directorate (ASD) 2. But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. Download Paper. The framework is designed to give security managers a reliable, systematic way to mitigate cyber risk no matter how complex the environment might be. A security policy is a declaration of intent about a companys resources. Having an ISMS is an important audit and compliance activity. The framework was taken over by the Center for Internet Security (CIS). NJ A.B. Center for Internet Security (CIS) Controls 4. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. Security Assessments Automate security questionnaire exchange. 1. Cyber Security is a body or a combination of technologies, processes, and practices that are defined and designed to protect computer systems, network systems and vital data from outside threats.

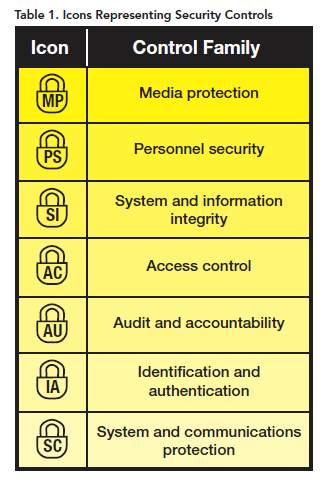
Australian Signals Directorate ( ASD) The ASD is an agency within the Australian government based in Canberra.
Cyber Security Standards and Frameworks Well-developed cyber security standards enable consistency among product developers and serve as a reliable metric for purchasing security products. In June 2020, the NSW Minister for Customer Service identified five key focuses for the Taskforce: Harmonising baseline standards and providing clarity for sector-specific additional standards and guidance. The challenge for an organization operating nationally, or even globally, is considerable. Test STIGs and test benchmarks were published from March through October 2020 to invite feedback. Risk-based, its a highly credible security management standard and also includes a mandatory assessment against GDPR requirements. This code, called EthicsfIRST, is supposed to guide anyone using computers in a meaningful way, including IT workers, students and influencers.EthicsfIRST outlines 12 duties people have when dealing with cybersecurity ethics..
OT Cybersecurity Standards and Guidelines Cybersecurity Legislation List of Cyber Security Regulations & Standards ISO 27000 series is developed and designed by the international organization for standardization and the International Electro-technical Commission.
desk clear security awareness cyber diary sans audit example isc checklist unacquainted standard month infosec handlers ten ms minutes created Application Software Security Solutions; Glossary of Cyber Security terms, definitions and acronyms Menu Toggle. PAS 555.
 cyber risk table level security defence matters industries ready implements particular appropriate contract supplier per below profile why
cyber risk table level security defence matters industries ready implements particular appropriate contract supplier per below profile why Naturally, every pape Relates to cyber security incident reporting and recommended cyber security standards for political subdivisions. Why?
nist csf cyber forgery and uttering; and; malicious communications.
Top 10 best practices for cybersecurity in 2022Use anti-malware software. One of the most important cybersecurity best practices is to install anti-malware software. Use strong, varied passwords. Another crucial cybersecurity step is to use strong passwords. Enable multifactor authentication. Verify before trusting. Update frequently. Encrypt where possible. Segment networks. More items The Department of Defense (DoD) announced the Cybersecurity Maturity Model Certification (CMMC) on January 31, 2020. Standard CIP-008 ensures the identification, classification, and reporting of cybersecurity Incidents related to critical cyber infrastructure. Variety of these cyber laws have been affected by broad framework principles given by the UNCITRAL Model Law on Electronic Commerce.

Besides, they contribute to international trade facilitation. Cybersecurity Publications - Frequently requested publications supporting DHSs cybersecurity priority and mission. ISO 27000 series helps to protect the data, employees, and privacy of the organization from cybercriminals. Cyber security is more than just an information technology problem.
frameworks cybersecurity pentestmag ISO27002:2013: this is an information security standard developed by ISO from BS7799 (British standard of information security).
An example of evidence may include, but is not limited to, a list of cyber security controls verified or tested along with the dated test results. ISO 27000 consists of an overview and vocabulary and defines ISMS program requirements.
donts dos Top 12 Cybersecurity Regulations for Financial Services IEEE, IETF, and the American National Standards Institute (ANSI). Blueprint for a Secure Cyber Future - The Cybersecurity Strategy for the Homeland Security Enterprise[PDF] National Institute of Standards and Technology (NIST) The organization must make sure that all changes are made in a thoughtful way that minimizes negative impact to services and customers. Nepal Telecommunications Authority (NTA), the Telecommunication regulatory body of Nepal, has implemented Cyber Security Bylaw 2077 (2020) recently.
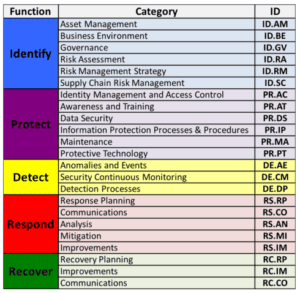
list of cyber security standards - univcofc.org 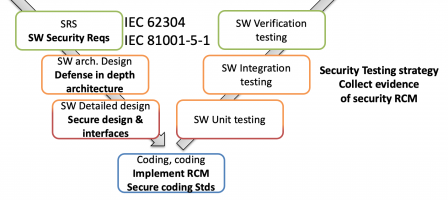 framework nist cybersecurity tiers detect respond protect identify recover risk compliance cyber security governance eagle eye implementation context provide
framework nist cybersecurity tiers detect respond protect identify recover risk compliance cyber security governance eagle eye implementation context provide The two primary standards -- ISO 27001 and 27002 -- establish the requirements and procedures for creating an information security management system ( ISMS ). Mitigate global supply chain risks. ISO 27001:2013 in particular is a risk-based standard approach for the information security management system.

The first two apply to us. Cybersecurity frameworks are often mandatory, or at least strongly encouraged, for companies that want to comply with state, industry, and international cybersecurity regulations. But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. Information Security Analyst is the top searched-for job by candidates and also the most requested cyber security job description by employers (see Top 10 list below).
Top 25 Cybersecurity Frameworks to Consider - SecurityScorecard Top 10 Australian Cybersecurity Frameworks in 2022 | UpGuard
Sitemap 9
 Standards Grade 7 salary.
Standards Grade 7 salary.  CISAs Role in Cybersecurity.
CISAs Role in Cybersecurity.  Essential Eight - Australian Signals Directorate (ASD) 2. But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. Download Paper. The framework is designed to give security managers a reliable, systematic way to mitigate cyber risk no matter how complex the environment might be. A security policy is a declaration of intent about a companys resources. Having an ISMS is an important audit and compliance activity. The framework was taken over by the Center for Internet Security (CIS). NJ A.B. Center for Internet Security (CIS) Controls 4. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. Security Assessments Automate security questionnaire exchange. 1. Cyber Security is a body or a combination of technologies, processes, and practices that are defined and designed to protect computer systems, network systems and vital data from outside threats.
Essential Eight - Australian Signals Directorate (ASD) 2. But the standards for cybersecurity compliance are different depending on what guidelines your organization is trying to comply with. Download Paper. The framework is designed to give security managers a reliable, systematic way to mitigate cyber risk no matter how complex the environment might be. A security policy is a declaration of intent about a companys resources. Having an ISMS is an important audit and compliance activity. The framework was taken over by the Center for Internet Security (CIS). NJ A.B. Center for Internet Security (CIS) Controls 4. First, if you want to achieve compliance for your business, you will need to meet certain compliance standards. Security Assessments Automate security questionnaire exchange. 1. Cyber Security is a body or a combination of technologies, processes, and practices that are defined and designed to protect computer systems, network systems and vital data from outside threats. 
 Australian Signals Directorate ( ASD) The ASD is an agency within the Australian government based in Canberra. Cyber Security Standards and Frameworks Well-developed cyber security standards enable consistency among product developers and serve as a reliable metric for purchasing security products. In June 2020, the NSW Minister for Customer Service identified five key focuses for the Taskforce: Harmonising baseline standards and providing clarity for sector-specific additional standards and guidance. The challenge for an organization operating nationally, or even globally, is considerable. Test STIGs and test benchmarks were published from March through October 2020 to invite feedback. Risk-based, its a highly credible security management standard and also includes a mandatory assessment against GDPR requirements. This code, called EthicsfIRST, is supposed to guide anyone using computers in a meaningful way, including IT workers, students and influencers.EthicsfIRST outlines 12 duties people have when dealing with cybersecurity ethics.. OT Cybersecurity Standards and Guidelines Cybersecurity Legislation List of Cyber Security Regulations & Standards ISO 27000 series is developed and designed by the international organization for standardization and the International Electro-technical Commission. desk clear security awareness cyber diary sans audit example isc checklist unacquainted standard month infosec handlers ten ms minutes created Application Software Security Solutions; Glossary of Cyber Security terms, definitions and acronyms Menu Toggle. PAS 555.
Australian Signals Directorate ( ASD) The ASD is an agency within the Australian government based in Canberra. Cyber Security Standards and Frameworks Well-developed cyber security standards enable consistency among product developers and serve as a reliable metric for purchasing security products. In June 2020, the NSW Minister for Customer Service identified five key focuses for the Taskforce: Harmonising baseline standards and providing clarity for sector-specific additional standards and guidance. The challenge for an organization operating nationally, or even globally, is considerable. Test STIGs and test benchmarks were published from March through October 2020 to invite feedback. Risk-based, its a highly credible security management standard and also includes a mandatory assessment against GDPR requirements. This code, called EthicsfIRST, is supposed to guide anyone using computers in a meaningful way, including IT workers, students and influencers.EthicsfIRST outlines 12 duties people have when dealing with cybersecurity ethics.. OT Cybersecurity Standards and Guidelines Cybersecurity Legislation List of Cyber Security Regulations & Standards ISO 27000 series is developed and designed by the international organization for standardization and the International Electro-technical Commission. desk clear security awareness cyber diary sans audit example isc checklist unacquainted standard month infosec handlers ten ms minutes created Application Software Security Solutions; Glossary of Cyber Security terms, definitions and acronyms Menu Toggle. PAS 555.  cyber risk table level security defence matters industries ready implements particular appropriate contract supplier per below profile why Naturally, every pape Relates to cyber security incident reporting and recommended cyber security standards for political subdivisions. Why? nist csf cyber forgery and uttering; and; malicious communications.
cyber risk table level security defence matters industries ready implements particular appropriate contract supplier per below profile why Naturally, every pape Relates to cyber security incident reporting and recommended cyber security standards for political subdivisions. Why? nist csf cyber forgery and uttering; and; malicious communications.  Top 10 best practices for cybersecurity in 2022Use anti-malware software. One of the most important cybersecurity best practices is to install anti-malware software. Use strong, varied passwords. Another crucial cybersecurity step is to use strong passwords. Enable multifactor authentication. Verify before trusting. Update frequently. Encrypt where possible. Segment networks. More items The Department of Defense (DoD) announced the Cybersecurity Maturity Model Certification (CMMC) on January 31, 2020. Standard CIP-008 ensures the identification, classification, and reporting of cybersecurity Incidents related to critical cyber infrastructure. Variety of these cyber laws have been affected by broad framework principles given by the UNCITRAL Model Law on Electronic Commerce.
Top 10 best practices for cybersecurity in 2022Use anti-malware software. One of the most important cybersecurity best practices is to install anti-malware software. Use strong, varied passwords. Another crucial cybersecurity step is to use strong passwords. Enable multifactor authentication. Verify before trusting. Update frequently. Encrypt where possible. Segment networks. More items The Department of Defense (DoD) announced the Cybersecurity Maturity Model Certification (CMMC) on January 31, 2020. Standard CIP-008 ensures the identification, classification, and reporting of cybersecurity Incidents related to critical cyber infrastructure. Variety of these cyber laws have been affected by broad framework principles given by the UNCITRAL Model Law on Electronic Commerce.  Besides, they contribute to international trade facilitation. Cybersecurity Publications - Frequently requested publications supporting DHSs cybersecurity priority and mission. ISO 27000 series helps to protect the data, employees, and privacy of the organization from cybercriminals. Cyber security is more than just an information technology problem. frameworks cybersecurity pentestmag ISO27002:2013: this is an information security standard developed by ISO from BS7799 (British standard of information security).
Besides, they contribute to international trade facilitation. Cybersecurity Publications - Frequently requested publications supporting DHSs cybersecurity priority and mission. ISO 27000 series helps to protect the data, employees, and privacy of the organization from cybercriminals. Cyber security is more than just an information technology problem. frameworks cybersecurity pentestmag ISO27002:2013: this is an information security standard developed by ISO from BS7799 (British standard of information security).  An example of evidence may include, but is not limited to, a list of cyber security controls verified or tested along with the dated test results. ISO 27000 consists of an overview and vocabulary and defines ISMS program requirements. donts dos Top 12 Cybersecurity Regulations for Financial Services IEEE, IETF, and the American National Standards Institute (ANSI). Blueprint for a Secure Cyber Future - The Cybersecurity Strategy for the Homeland Security Enterprise[PDF] National Institute of Standards and Technology (NIST) The organization must make sure that all changes are made in a thoughtful way that minimizes negative impact to services and customers. Nepal Telecommunications Authority (NTA), the Telecommunication regulatory body of Nepal, has implemented Cyber Security Bylaw 2077 (2020) recently. list of cyber security standards - univcofc.org
An example of evidence may include, but is not limited to, a list of cyber security controls verified or tested along with the dated test results. ISO 27000 consists of an overview and vocabulary and defines ISMS program requirements. donts dos Top 12 Cybersecurity Regulations for Financial Services IEEE, IETF, and the American National Standards Institute (ANSI). Blueprint for a Secure Cyber Future - The Cybersecurity Strategy for the Homeland Security Enterprise[PDF] National Institute of Standards and Technology (NIST) The organization must make sure that all changes are made in a thoughtful way that minimizes negative impact to services and customers. Nepal Telecommunications Authority (NTA), the Telecommunication regulatory body of Nepal, has implemented Cyber Security Bylaw 2077 (2020) recently. list of cyber security standards - univcofc.org  framework nist cybersecurity tiers detect respond protect identify recover risk compliance cyber security governance eagle eye implementation context provide The two primary standards -- ISO 27001 and 27002 -- establish the requirements and procedures for creating an information security management system ( ISMS ). Mitigate global supply chain risks. ISO 27001:2013 in particular is a risk-based standard approach for the information security management system.
framework nist cybersecurity tiers detect respond protect identify recover risk compliance cyber security governance eagle eye implementation context provide The two primary standards -- ISO 27001 and 27002 -- establish the requirements and procedures for creating an information security management system ( ISMS ). Mitigate global supply chain risks. ISO 27001:2013 in particular is a risk-based standard approach for the information security management system.