Where can I find the example code for the Azure Database SQL Server Server Vulnerability Assessment? Playbook Remediation. The steps include the following: Discover: Identify vulnerabilities through testing and scanning. It can also be integrated with pre-commit.If you want, it can be applied to Bicep, Kubernetes or other supported frameworks.
Auditing Terraform Open Source for Security, Governance, Risk 
More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects.
Vulnerability opencti-terraform code analysis shows 2 unresolved vulnerabilities (0 blocker, 1 critical, 0 major, 1 minor). Cloud native security research, vulnerabilities, security threats & alerts, analysis of attacks. Terraform must keep track of the resources created. Deploy the tutorial app using Schematics, Terraform, and a Tekton-based pipeline.

Consumers are timely manner to address emerging vulnerabilities. You can do this using --no-colour (or --no-color for our American friends). opencti-terraform has no vulnerabilities reported, and its dependent libraries have no vulnerabilities reported.
Cloud Code Security Then I used the below code for the requirement that you have : Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices.
terraform vsphere ubuntu vmware It is not recommended for customers to store any personal data in Terraform Cloud. KICS is easy to install and run, easy to understand results, and easy to integrate into CI.
 terraform vsphere Cyber Security News Complete Guide
terraform vsphere Cyber Security News Complete Guide  Introducing TerraGoat, a vulnerable-by-design Terraform lacework terraform automate
Introducing TerraGoat, a vulnerable-by-design Terraform lacework terraform automate Although Terraform is an amazing tool for IaC, it may not validate issues that are provider-specific.
kics queries 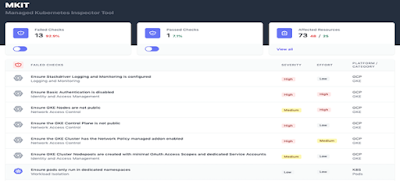
Explore security best practices for a strong Terraform setup. We apply best practices and focus on security to make sure we can maintain the trust of the community. It works under 64-bit systems in Windows, Linux and macOS environments, and can analyze source code intended for 32-bit, 64-bit and embedded ARM platforms.
Vulnerability Terraform Security Vulnerabilities  Security | Terraform by HashiCorp Terraform
Security | Terraform by HashiCorp Terraform format our code (style, syntax, indentation etc.)
Security Command Center Vulnerability KICS - Keeping Infrastructure as Code Secure Last time I wrote about getting started with pre-commit.This time I want to write a little more on how you can use checkov to

Playbook Remediation.
terraform vulnerabilities July 2019. pylint.
Terraform If you read the blog "IBM Cloud Solution Tutorials: 2020 in Review," you will have noticed that the IBM Cloud Solution Tutorials can now also be found in a new tutorials library in the IBM Cloud documentation portal.One of these tutorials from the Security category is discussing This section takes you step by step through building a Google Cloud deployment with a secured foundation that you can use to run workloads securely in the cloud.
Terraform Security: Resource Does Not Have Attribute In 2022 there have been 0 vulnerabilities in HashiCorp Terraform . There are active, dedicated users willing to help you through various mediums. Vulnerability Management plays a crucial role in monitoring an organizations overall security posture. Terraform is increasingly used to automate deployment of mission critical, production systems.
Snyk brings infrastructure as code security to HashiCorp Terraform Overview; Infrastructure automation workflow featuring security, compliance, and cost management capabilities while using access controls, policy enforcement, and audit. Weekly Hours: 40. GitHub Terraform Cloud.
vuls freebsd vulnerability abstract One of the core components of IAM is the policy which, when attached to an identity or a resource, defines its permissions. Terraform is an awesome tool to deploy and update your infrastructure using code. You might be using it already to automate your clusters deployment in cloud providers like AWS, Google Cloud, Azure or IBM. The good news is that now you can configure your container security as code with Terraform and Sysdig Secure. For Terraform, the prancer-io/prancer-terramerra, davesee/terraform-caf-rover-breakout and anmoltoppo/Terraform source code examples are useful.
Security Vulnerabilities Security Aqua adds free infrastructure-as-code security for Terraform AWS Identity and Access Management (IAM) is the service that defines access to AWS resources.
Terraform Security | Prevent Terraform Misconfigurations reconnaissance vulnerability scanning automated 
We understand that many users place a high level of trust in HashiCorp and the tools we build. Terrascan is an infrastructure as Code (IaC) security scanner.
lacework terraform bridgecrew vulnerabilities Implement third-party solutions such as Terraform to create a configuration file that declares the resources for the Kubernetes cluster. At the same time, using infrastructure as code (IaC) tools like This enables developers to shift IaC security left and make Terraform security an integral part of the development process.
Hashicorp Terraform : List of security vulnerabilities Manage and Remediate Cloud Infrastructure Misconfiguration 1:26:00 Import hashicorp-demoapp/frontend to Snyk (for vulnerability scanning on PRs)
Terraform Terraform is an open-source infrastructure as code software tool that enables you to safely and predictably create, change, and improve infrastructure.
Complete Guide to Terraform Cloud Security - TMCnet Enable Strict Transport Security Header One of the most significant advantages of implementing container security as code with Sysdig Secure Terraform provider is having a reproducible version-controlled security policy. Having missing or misconfigured variables in IaC modules, you may be inadvertently deploying vulnerable cloud resources. I enabled System Managed Identity on the existing SQL Server and then provided Storage Blob Data Contributor from terraform code. So, what
Security Overview NiushaDastan/VPC-with-Terraform GitHub Current Description.
Terraform Catalog | Security Journey Community Forum. Compare the best Terraform alternatives in 2022.
vulnerability Security policy Active. Recommendation
vuls freebsd vulnerability Checking Terraform IaC security in CI/CD with Regula and Travis CI 31:00 Triaging Vulnerabilities. aws.

Write secure Terraform modules.
Terraform for Beginners and language-specific packages (Bundler, Composer, npm, yarn, etc.). How do I get this information (LicenseCode, CustomerID, and Resource ID) for writing in my .tf files? More details can be found on the Terraform Cloud Data Security page.
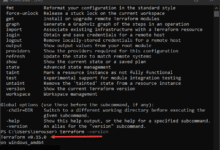
CloudGoat is used to deploy (and shutdown) a vulnerable set of AWS resources, designed to teach AWS security risks. If you become aware of a security vulnerability affecting the Terraform binary version installed on your Terraform server, switch to a version that is not affected by the vulnerability. Setting up the integration of Snyk into Terraform cloud is very easy to do: First you need an account on Snyk.io, I have chosen to use a free account which gets me 300 IaC scans per month.
How to Use Amazon Inspector With Terraform - DZone Security Where can I find the example code for the Azure Database SQL Server Server Vulnerability Assessment? Last year, the average CVE base score was greater by 0.15 Kube Hunter is a vulnerability scanning tool by Aqua Security for your Kubernetes cluster. At the current rates, it appears that the number of vulnerabilities last year and this year may equal out.
Terraform Registry Then you get an endpoint URL from you Synk account and a HMAC key. This open-source tool allows users to create, update, and manage cloud resources.
checkov misconfigurations cloudformation kubernetes terraform prevent releases 12. minutes. Our solution identifies and remediates OWASP TOP 10/API TOP 10 code vulnerabilities of cloud native apps. Coming soon: Azure & GCP Domains AWS S3 Buckets, Permissions, Encryption at Rest, Encryption in Transit & Traceability Get started analyzing
Security Kubernetes Scanner to find Security Vulnerability and I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. 7 Terraform Security Best Practices.
terraform Attributes Reference. Mazin Ahmed is a security engineer that specializes in AppSec and offensive security. In addition to Linux, the threat and vulnerability management capabilities already support macOS and Windows, with support for Android and iOS coming later this summer to further expand our support of third party platforms. Last year Terraform had 1 security vulnerability published. Published: 12 Jul 2021. More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects.
Protect the state by using remote backend plugins in tandem with sound access control policies.
Terraform Cloud Security & Compliance White Paper Note that turning this on incurs a monthly cost per server. Key areas of concerns for vulnerability management for Terraform environments include: Secrets Management: Terraform requires credentials in order to authorize any API actions necessary to provision the infrastructure specified in your code. Secure State provides Risk Scores, so you can prioritize security vulnerabilities and violations based on blast radius and quantified risk severity. I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. Security overview. We deeply appreciate any effort to disclose vulnerabilities responsibly. There are 14 security hotspots that need review. They add the ability to an identity to perform Unlike with security vulnerabilities, there is no common system to rank how dangerous a misconfiguration can be. Security Hotspot. Read in English. 2000+ queries are available.

This issue impacts Checkov 2.0 versions earlier than View security policy. Using the Terraform example.
Prevent cloud misconfigurations in HashiCorp Terraform with Snyk terrafirma vulnerabilities Terraform can improve your security posture - by applying security policies as code, maintaining a registry of trusted modules, and encrypting vaults and secrets to keep them secure from attackers. The security of example.com takes a unified approach to governance, security objectives, compliance, identity, connectivity, and workloads.
Security Overview hashicorp/terraform GitHub nsx terraform firewall Vulnerability Bridgecrew: Misconfigured Terraform Modules Are a Security Issue  Terraform
Terraform GitHub is where people build software. Terraform Security with Atlantis and Terrascan. validate the conformity of the code (monitoring of Terraform standards, good practices to be respected according to each provider used) It allows users to fix vulnerable infrastructure before it is ever deployed. Supported by industry-leading application and security intelligence, Snyk puts security expertise in any developer's toolkit.
devops terraform gitlab : CVE-2009-1234 or 2010-1234 or 20101234) Log In Register Take a third party risk management course for FREE.
NVD - CVE-2021-40862 5.1: Run automated vulnerability scanning tools. Role Number: 200213446. In order to prevent misconfiguration, additional Terraform security scanning is crucial. Terraform enables you to embed cloud security earlier and leverage automation and code to secure it. By scanning your Terraform modules earlier in the development lifecycle you can actually prevent misconfigurations from being deployed. Run a code playbook to remediate an issue rather than having to go through a manual process to do so.
Creating SQL Server vulnerability assessment resource using KICS finds security vulnerabilities, compliance issues, and infrastructure misconfigurations in the following Infrastructure as Code solutions: Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Microsoft ARM.
Sitemap 6
 More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects. Vulnerability opencti-terraform code analysis shows 2 unresolved vulnerabilities (0 blocker, 1 critical, 0 major, 1 minor). Cloud native security research, vulnerabilities, security threats & alerts, analysis of attacks. Terraform must keep track of the resources created. Deploy the tutorial app using Schematics, Terraform, and a Tekton-based pipeline.
More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects. Vulnerability opencti-terraform code analysis shows 2 unresolved vulnerabilities (0 blocker, 1 critical, 0 major, 1 minor). Cloud native security research, vulnerabilities, security threats & alerts, analysis of attacks. Terraform must keep track of the resources created. Deploy the tutorial app using Schematics, Terraform, and a Tekton-based pipeline.  Consumers are timely manner to address emerging vulnerabilities. You can do this using --no-colour (or --no-color for our American friends). opencti-terraform has no vulnerabilities reported, and its dependent libraries have no vulnerabilities reported. Cloud Code Security Then I used the below code for the requirement that you have : Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices. terraform vsphere ubuntu vmware It is not recommended for customers to store any personal data in Terraform Cloud. KICS is easy to install and run, easy to understand results, and easy to integrate into CI.
Consumers are timely manner to address emerging vulnerabilities. You can do this using --no-colour (or --no-color for our American friends). opencti-terraform has no vulnerabilities reported, and its dependent libraries have no vulnerabilities reported. Cloud Code Security Then I used the below code for the requirement that you have : Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices. terraform vsphere ubuntu vmware It is not recommended for customers to store any personal data in Terraform Cloud. KICS is easy to install and run, easy to understand results, and easy to integrate into CI.  terraform vsphere Cyber Security News Complete Guide
terraform vsphere Cyber Security News Complete Guide  Introducing TerraGoat, a vulnerable-by-design Terraform lacework terraform automate Although Terraform is an amazing tool for IaC, it may not validate issues that are provider-specific. kics queries
Introducing TerraGoat, a vulnerable-by-design Terraform lacework terraform automate Although Terraform is an amazing tool for IaC, it may not validate issues that are provider-specific. kics queries  Explore security best practices for a strong Terraform setup. We apply best practices and focus on security to make sure we can maintain the trust of the community. It works under 64-bit systems in Windows, Linux and macOS environments, and can analyze source code intended for 32-bit, 64-bit and embedded ARM platforms. Vulnerability Terraform Security Vulnerabilities
Explore security best practices for a strong Terraform setup. We apply best practices and focus on security to make sure we can maintain the trust of the community. It works under 64-bit systems in Windows, Linux and macOS environments, and can analyze source code intended for 32-bit, 64-bit and embedded ARM platforms. Vulnerability Terraform Security Vulnerabilities  Security | Terraform by HashiCorp Terraform format our code (style, syntax, indentation etc.) Security Command Center Vulnerability KICS - Keeping Infrastructure as Code Secure Last time I wrote about getting started with pre-commit.This time I want to write a little more on how you can use checkov to
Security | Terraform by HashiCorp Terraform format our code (style, syntax, indentation etc.) Security Command Center Vulnerability KICS - Keeping Infrastructure as Code Secure Last time I wrote about getting started with pre-commit.This time I want to write a little more on how you can use checkov to  Playbook Remediation. terraform vulnerabilities July 2019. pylint. Terraform If you read the blog "IBM Cloud Solution Tutorials: 2020 in Review," you will have noticed that the IBM Cloud Solution Tutorials can now also be found in a new tutorials library in the IBM Cloud documentation portal.One of these tutorials from the Security category is discussing This section takes you step by step through building a Google Cloud deployment with a secured foundation that you can use to run workloads securely in the cloud. Terraform Security: Resource Does Not Have Attribute In 2022 there have been 0 vulnerabilities in HashiCorp Terraform . There are active, dedicated users willing to help you through various mediums. Vulnerability Management plays a crucial role in monitoring an organizations overall security posture. Terraform is increasingly used to automate deployment of mission critical, production systems. Snyk brings infrastructure as code security to HashiCorp Terraform Overview; Infrastructure automation workflow featuring security, compliance, and cost management capabilities while using access controls, policy enforcement, and audit. Weekly Hours: 40. GitHub Terraform Cloud. vuls freebsd vulnerability abstract One of the core components of IAM is the policy which, when attached to an identity or a resource, defines its permissions. Terraform is an awesome tool to deploy and update your infrastructure using code. You might be using it already to automate your clusters deployment in cloud providers like AWS, Google Cloud, Azure or IBM. The good news is that now you can configure your container security as code with Terraform and Sysdig Secure. For Terraform, the prancer-io/prancer-terramerra, davesee/terraform-caf-rover-breakout and anmoltoppo/Terraform source code examples are useful. Security Vulnerabilities Security Aqua adds free infrastructure-as-code security for Terraform AWS Identity and Access Management (IAM) is the service that defines access to AWS resources. Terraform Security | Prevent Terraform Misconfigurations reconnaissance vulnerability scanning automated
Playbook Remediation. terraform vulnerabilities July 2019. pylint. Terraform If you read the blog "IBM Cloud Solution Tutorials: 2020 in Review," you will have noticed that the IBM Cloud Solution Tutorials can now also be found in a new tutorials library in the IBM Cloud documentation portal.One of these tutorials from the Security category is discussing This section takes you step by step through building a Google Cloud deployment with a secured foundation that you can use to run workloads securely in the cloud. Terraform Security: Resource Does Not Have Attribute In 2022 there have been 0 vulnerabilities in HashiCorp Terraform . There are active, dedicated users willing to help you through various mediums. Vulnerability Management plays a crucial role in monitoring an organizations overall security posture. Terraform is increasingly used to automate deployment of mission critical, production systems. Snyk brings infrastructure as code security to HashiCorp Terraform Overview; Infrastructure automation workflow featuring security, compliance, and cost management capabilities while using access controls, policy enforcement, and audit. Weekly Hours: 40. GitHub Terraform Cloud. vuls freebsd vulnerability abstract One of the core components of IAM is the policy which, when attached to an identity or a resource, defines its permissions. Terraform is an awesome tool to deploy and update your infrastructure using code. You might be using it already to automate your clusters deployment in cloud providers like AWS, Google Cloud, Azure or IBM. The good news is that now you can configure your container security as code with Terraform and Sysdig Secure. For Terraform, the prancer-io/prancer-terramerra, davesee/terraform-caf-rover-breakout and anmoltoppo/Terraform source code examples are useful. Security Vulnerabilities Security Aqua adds free infrastructure-as-code security for Terraform AWS Identity and Access Management (IAM) is the service that defines access to AWS resources. Terraform Security | Prevent Terraform Misconfigurations reconnaissance vulnerability scanning automated  We understand that many users place a high level of trust in HashiCorp and the tools we build. Terrascan is an infrastructure as Code (IaC) security scanner. lacework terraform bridgecrew vulnerabilities Implement third-party solutions such as Terraform to create a configuration file that declares the resources for the Kubernetes cluster. At the same time, using infrastructure as code (IaC) tools like This enables developers to shift IaC security left and make Terraform security an integral part of the development process. Hashicorp Terraform : List of security vulnerabilities Manage and Remediate Cloud Infrastructure Misconfiguration 1:26:00 Import hashicorp-demoapp/frontend to Snyk (for vulnerability scanning on PRs) Terraform Terraform is an open-source infrastructure as code software tool that enables you to safely and predictably create, change, and improve infrastructure. Complete Guide to Terraform Cloud Security - TMCnet Enable Strict Transport Security Header One of the most significant advantages of implementing container security as code with Sysdig Secure Terraform provider is having a reproducible version-controlled security policy. Having missing or misconfigured variables in IaC modules, you may be inadvertently deploying vulnerable cloud resources. I enabled System Managed Identity on the existing SQL Server and then provided Storage Blob Data Contributor from terraform code. So, what Security Overview NiushaDastan/VPC-with-Terraform GitHub Current Description. Terraform Catalog | Security Journey Community Forum. Compare the best Terraform alternatives in 2022. vulnerability Security policy Active. Recommendation vuls freebsd vulnerability Checking Terraform IaC security in CI/CD with Regula and Travis CI 31:00 Triaging Vulnerabilities. aws.
We understand that many users place a high level of trust in HashiCorp and the tools we build. Terrascan is an infrastructure as Code (IaC) security scanner. lacework terraform bridgecrew vulnerabilities Implement third-party solutions such as Terraform to create a configuration file that declares the resources for the Kubernetes cluster. At the same time, using infrastructure as code (IaC) tools like This enables developers to shift IaC security left and make Terraform security an integral part of the development process. Hashicorp Terraform : List of security vulnerabilities Manage and Remediate Cloud Infrastructure Misconfiguration 1:26:00 Import hashicorp-demoapp/frontend to Snyk (for vulnerability scanning on PRs) Terraform Terraform is an open-source infrastructure as code software tool that enables you to safely and predictably create, change, and improve infrastructure. Complete Guide to Terraform Cloud Security - TMCnet Enable Strict Transport Security Header One of the most significant advantages of implementing container security as code with Sysdig Secure Terraform provider is having a reproducible version-controlled security policy. Having missing or misconfigured variables in IaC modules, you may be inadvertently deploying vulnerable cloud resources. I enabled System Managed Identity on the existing SQL Server and then provided Storage Blob Data Contributor from terraform code. So, what Security Overview NiushaDastan/VPC-with-Terraform GitHub Current Description. Terraform Catalog | Security Journey Community Forum. Compare the best Terraform alternatives in 2022. vulnerability Security policy Active. Recommendation vuls freebsd vulnerability Checking Terraform IaC security in CI/CD with Regula and Travis CI 31:00 Triaging Vulnerabilities. aws.  Write secure Terraform modules. Terraform for Beginners and language-specific packages (Bundler, Composer, npm, yarn, etc.). How do I get this information (LicenseCode, CustomerID, and Resource ID) for writing in my .tf files? More details can be found on the Terraform Cloud Data Security page.
Write secure Terraform modules. Terraform for Beginners and language-specific packages (Bundler, Composer, npm, yarn, etc.). How do I get this information (LicenseCode, CustomerID, and Resource ID) for writing in my .tf files? More details can be found on the Terraform Cloud Data Security page.  CloudGoat is used to deploy (and shutdown) a vulnerable set of AWS resources, designed to teach AWS security risks. If you become aware of a security vulnerability affecting the Terraform binary version installed on your Terraform server, switch to a version that is not affected by the vulnerability. Setting up the integration of Snyk into Terraform cloud is very easy to do: First you need an account on Snyk.io, I have chosen to use a free account which gets me 300 IaC scans per month. How to Use Amazon Inspector With Terraform - DZone Security Where can I find the example code for the Azure Database SQL Server Server Vulnerability Assessment? Last year, the average CVE base score was greater by 0.15 Kube Hunter is a vulnerability scanning tool by Aqua Security for your Kubernetes cluster. At the current rates, it appears that the number of vulnerabilities last year and this year may equal out. Terraform Registry Then you get an endpoint URL from you Synk account and a HMAC key. This open-source tool allows users to create, update, and manage cloud resources. checkov misconfigurations cloudformation kubernetes terraform prevent releases 12. minutes. Our solution identifies and remediates OWASP TOP 10/API TOP 10 code vulnerabilities of cloud native apps. Coming soon: Azure & GCP Domains AWS S3 Buckets, Permissions, Encryption at Rest, Encryption in Transit & Traceability Get started analyzing Security Kubernetes Scanner to find Security Vulnerability and I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. 7 Terraform Security Best Practices. terraform Attributes Reference. Mazin Ahmed is a security engineer that specializes in AppSec and offensive security. In addition to Linux, the threat and vulnerability management capabilities already support macOS and Windows, with support for Android and iOS coming later this summer to further expand our support of third party platforms. Last year Terraform had 1 security vulnerability published. Published: 12 Jul 2021. More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects. Protect the state by using remote backend plugins in tandem with sound access control policies. Terraform Cloud Security & Compliance White Paper Note that turning this on incurs a monthly cost per server. Key areas of concerns for vulnerability management for Terraform environments include: Secrets Management: Terraform requires credentials in order to authorize any API actions necessary to provision the infrastructure specified in your code. Secure State provides Risk Scores, so you can prioritize security vulnerabilities and violations based on blast radius and quantified risk severity. I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. Security overview. We deeply appreciate any effort to disclose vulnerabilities responsibly. There are 14 security hotspots that need review. They add the ability to an identity to perform Unlike with security vulnerabilities, there is no common system to rank how dangerous a misconfiguration can be. Security Hotspot. Read in English. 2000+ queries are available.
CloudGoat is used to deploy (and shutdown) a vulnerable set of AWS resources, designed to teach AWS security risks. If you become aware of a security vulnerability affecting the Terraform binary version installed on your Terraform server, switch to a version that is not affected by the vulnerability. Setting up the integration of Snyk into Terraform cloud is very easy to do: First you need an account on Snyk.io, I have chosen to use a free account which gets me 300 IaC scans per month. How to Use Amazon Inspector With Terraform - DZone Security Where can I find the example code for the Azure Database SQL Server Server Vulnerability Assessment? Last year, the average CVE base score was greater by 0.15 Kube Hunter is a vulnerability scanning tool by Aqua Security for your Kubernetes cluster. At the current rates, it appears that the number of vulnerabilities last year and this year may equal out. Terraform Registry Then you get an endpoint URL from you Synk account and a HMAC key. This open-source tool allows users to create, update, and manage cloud resources. checkov misconfigurations cloudformation kubernetes terraform prevent releases 12. minutes. Our solution identifies and remediates OWASP TOP 10/API TOP 10 code vulnerabilities of cloud native apps. Coming soon: Azure & GCP Domains AWS S3 Buckets, Permissions, Encryption at Rest, Encryption in Transit & Traceability Get started analyzing Security Kubernetes Scanner to find Security Vulnerability and I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. 7 Terraform Security Best Practices. terraform Attributes Reference. Mazin Ahmed is a security engineer that specializes in AppSec and offensive security. In addition to Linux, the threat and vulnerability management capabilities already support macOS and Windows, with support for Android and iOS coming later this summer to further expand our support of third party platforms. Last year Terraform had 1 security vulnerability published. Published: 12 Jul 2021. More than 83 million people use GitHub to discover, fork, and contribute to over 200 million projects. Protect the state by using remote backend plugins in tandem with sound access control policies. Terraform Cloud Security & Compliance White Paper Note that turning this on incurs a monthly cost per server. Key areas of concerns for vulnerability management for Terraform environments include: Secrets Management: Terraform requires credentials in order to authorize any API actions necessary to provision the infrastructure specified in your code. Secure State provides Risk Scores, so you can prioritize security vulnerabilities and violations based on blast radius and quantified risk severity. I'm trying to install Virtual Machine Vulnerability Assessment (powered by Qualys) extension via Terraform. Security overview. We deeply appreciate any effort to disclose vulnerabilities responsibly. There are 14 security hotspots that need review. They add the ability to an identity to perform Unlike with security vulnerabilities, there is no common system to rank how dangerous a misconfiguration can be. Security Hotspot. Read in English. 2000+ queries are available.  This issue impacts Checkov 2.0 versions earlier than View security policy. Using the Terraform example. Prevent cloud misconfigurations in HashiCorp Terraform with Snyk terrafirma vulnerabilities Terraform can improve your security posture - by applying security policies as code, maintaining a registry of trusted modules, and encrypting vaults and secrets to keep them secure from attackers. The security of example.com takes a unified approach to governance, security objectives, compliance, identity, connectivity, and workloads. Security Overview hashicorp/terraform GitHub nsx terraform firewall Vulnerability Bridgecrew: Misconfigured Terraform Modules Are a Security Issue
This issue impacts Checkov 2.0 versions earlier than View security policy. Using the Terraform example. Prevent cloud misconfigurations in HashiCorp Terraform with Snyk terrafirma vulnerabilities Terraform can improve your security posture - by applying security policies as code, maintaining a registry of trusted modules, and encrypting vaults and secrets to keep them secure from attackers. The security of example.com takes a unified approach to governance, security objectives, compliance, identity, connectivity, and workloads. Security Overview hashicorp/terraform GitHub nsx terraform firewall Vulnerability Bridgecrew: Misconfigured Terraform Modules Are a Security Issue