scaling terraform elb insidepacket Valid values are HTTP, HTTPS, or #{protocol}. The others go to the host https://redirect.to. A map of tags assigned to the resource, including those inherited from the provider default_tags configuration block. Defaults to #{protocol}.
Valid values are HTTP1Only, HTTP2Only, HTTP2Optional, HTTP2Preferred, and None. Fixed-response Blocks (for fixed_response) support the following: Authenticate Cognito Blocks (for authenticate_cognito) supports the following: Authenticate OIDC Blocks (for authenticate_oidc) supports the following: Authentication Request Extra Params Blocks (for authentication_request_extra_params) supports the following: Condition Blocks (for condition) support the following: The following attributes are exported in addition to the arguments listed above: Rules can be imported using their ARN, e.g.
scaling elb terraform aws Specify only when type is authenticate-cognito.
practitioner https://www.terraform.io/docs/providers/aws/r/lb_listener.html, https://github.com/terraform-providers/terraform-provider-aws/blob/master/aws/data_source_aws_lb_listener.go#L39, https://www.terraform.io/docs/providers/aws/r/lb_listener_rule.html, https://www.hashicorp.com/community-guidelines.html, https://github.com/hashicorp/terraform/issues, terraform-tool+unsubscribe@googlegroups.com, https://groups.google.com/d/msgid/terraform-tool/572724f8-9616-46ff-8e3d-c7d1c11a5c5c%40googlegroups.com.
terraform elb scaling aws Pass worker_target_groups to the cluster to register worker instances into custom target groups. You can see details below: I hope, this trick is helpful to you.Edit on June 28, 2022: I used this code block on https://github.com/flightlesstux/antmedia/tree/master/aws-cluster You can check and understand hows working.
vmware integrating Name of the cookie used to maintain session information. Lets use the data source for retrieving the ARN this time. Default is false. Clusters with multiple controllers span zones in a region to tolerate zone outages. Defaults to /#{path}.

Exactly one certificate is required if the protocol is HTTPS.
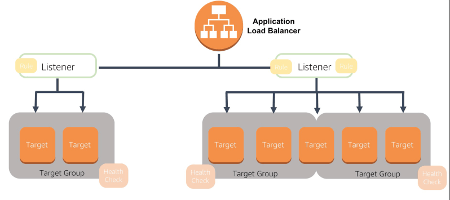
First, we need to create the ALB itself. AWS NLBs and target groups do not support UDP, Global Accelerator does support UDP, but its expensive. If I'm wrong can I see an example of multiple routing rules pointing to different target groups? Detailed below. It allows us to write the wireframe of the cloud infrastructure we use by simple configuration language called HCL.
elb on loadbalancing.tf line 25, in resource aws_lb_listener ecs_cluster_listener: Hostname. Required fields are marked *.
The action with the lowest value for order is performed first.
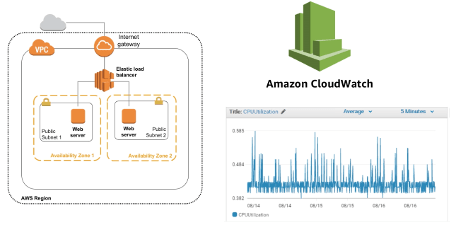
elb terraform Behavior if the user is not authenticated. ARN of the default SSL server certificate. A network load balancer (NLB) distributes IPv4 TCP/80 and TCP/443 traffic across two target groups of worker nodes with a healthy Ingress controller. Name of the SSL Policy for the listener.
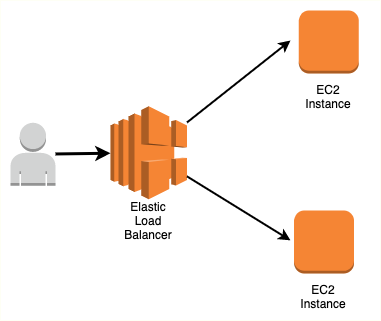
Max: 10. Today, Im going to show you how to construct the application load balancer in AWS with Terraform. Error: Unsupported block type
elb asg Workers span the zones in a region to tolerate zone outages. If no other actions are matched, the default action will be taken.
aws deployments alb downtime zero appoptics load Next, we can attach a listener to the ALB we have created.

A network load balancer (NLB) distributes IPv4 TCP/6443 traffic across a target group of controller nodes with a healthy kube-apiserver.
Terraformer accelerates the Terraform migration process, How to add new policy to IAM role by Terraform, True Cause behind Additional Verification in ACM. Configuration block for an identity provider that is compliant with OpenID Connect (OIDC). #Bag of options to control resource's behavior. This component is not percent-encoded. This component is not percent-encoded. Add a custom route to the VPC route table.

Detailed below.
All input properties are implicitly available as output properties.
Can be set if protocol is TLS.
elb ec2 asg aws balancing elb The alias record is output as ingress_dns_name for use in application DNS CNAME records. Thanks to that, we can safely modify the underlying infrastructure and quickly track the history of the change. The range is 1-604800 seconds (7 days). Defaults to #{host}. You do not have permission to delete messages in this group, Either email addresses are anonymous for this group or you need the view member email addresses permission to view the original message.

To learn more about resource properties and how to use them, see Inputs and Outputs in the Architecture and Concepts docs.
If you specify both forward block and target_group_arn attribute, you can specify only one target group using forward and it must be the same target group specified in target_group_arn.
A map of tags to assign to the resource.
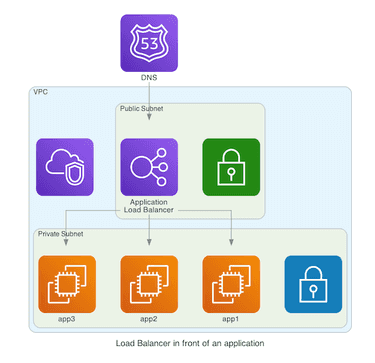
Note that this listener has a default action.
proxy alb nginx aws reverse signed behind self tls load which Additionally, the Listener resource produces the following output properties: The provider-assigned unique ID for this managed resource. "${aws_cognito_user_pool_client.client.id}", "${aws_cognito_user_pool_domain.domain.domain}", "https://example.com/authorization_endpoint". I didnt try on CodeDeploy.
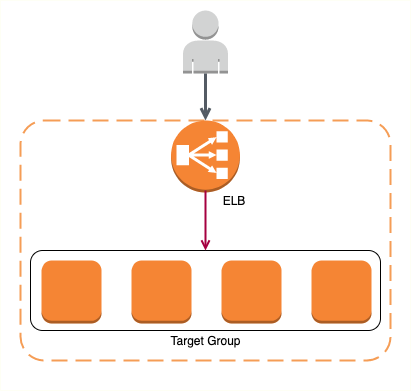
In my case, I need to forward the traffic from AWS Application Load Balancer public interface to two different target groups. Finally, I found a solution to my case for my own. $ pulumi import aws:lb/listener:Listener front_end arn:aws:elasticloadbalancing:us-west-2:187416307283:listener/app/front-end-alb/8e4497da625e2d8a/9ab28ade35828f96. Note: aws.alb.Listener is known as aws.lb.Listener. This value is required for rules with multiple actions. Blocks of type target_group are not expected here.
 listener configure externally nlb
listener configure externally nlb Detailed below. Valid values are between 1 and 50000.
balancer elb balancers ec2 scaling fargate aws tracking target policy medium template cloudwatch stack attached launch sample using create Lastly, you can add your custom rules as you like with aws_lb_listener_rule. When I try a similar configuration, CodeDeploy complains that:
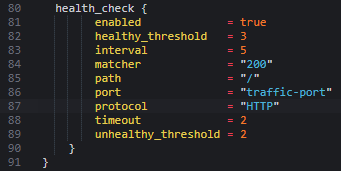
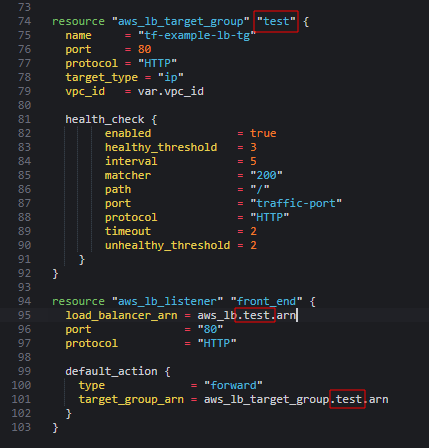
Required if protocol is HTTPS or TLS. aws_lb resource will form the ALB as follows. The Listener resource accepts the following input properties: Configuration block for default actions. Detailed below. Provides a Load Balancer Listener Rule resource. Specify only when type is authenticate-oidc. Defaults to #{query}. Your email address will not be published. Listeners can be imported using their ARN, e.g.. ARN of the Target Group to which to route traffic.
Once the Terraform configuration is written, we can get the same resource by just applying it. The redirect is either permanent (HTTP_301) or temporary (HTTP_302). Maximum duration of the authentication session, in seconds.

Name of the Application-Layer Protocol Negotiation (ALPN) policy. Set of 1-5 target group blocks. Content type. Specify only if type is forward and you want to route to a single target group. A listener and target group may map different ports (e.g 3333 external, 30333 internal). To route to one or more target groups, use a forward block instead. This allows you to decouple the definition of the rules to a different project or different set of logic, and also matches the actual AWS API for these resources, which treats them as a separate resource. Type of routing action.
practitioner cloud 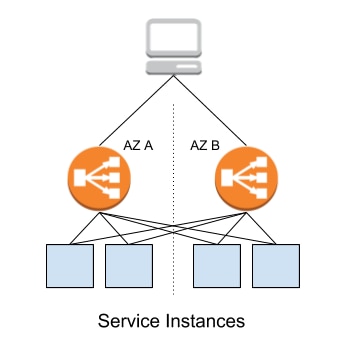
Absolute path, starting with the leading "/". Add firewall rules to the worker security group.



Maybe something is changed on AWS or TF side and needs to be refactored. This action returns a 301 response with the redirection to the specific location by local.redirect_to. 25: target_group { All requests matching with the path /forward_to/* are routed to the target group this_tg. Detailed below. Protocol. Configuration block for target group stickiness for the rule.

Time period, in seconds, during which requests from a client should be routed to the same target group. Detailed below. Thanks David! Configuration block for using Amazon Cognito to authenticate users.
balancer provisioning terraform application vpc assuming 
Defaults to #{port}. That is what I did to prepare the load balancer running in front of our service. Get an existing Listener resources state with the given name, ID, and optional extra properties used to qualify the lookup. Query parameters, URL-encoded when necessary, but not percent-encoded.

The hashicorp language (HCL) not a hard language but the document is missing a lot of subjects and also there are some points in terraform are undocumented.Ive Google it before the make sure but Ive seen there is a lot of questions and issues about the Use more than one target group on AWS with terraform subject.I read the suggested solutions but they do not help me.

The path can contain #{host}, #{path}, and #{port}. Set two different Target Groups on AWS Load Balancer with Terraform. Provides a Load Balancer Listener resource. The ELB could not be updated due to the following error: Green taskset target group cannot have non-zero weight prior to traffic shifting on listener arn:aws:elasticloadbalancing:.etc. Configuration block for creating an action that distributes requests among one or more target groups. Information for creating an action that returns a custom HTTP response. Valid values: deny, allow and authenticate. Save my name, email, and website in this browser for the next time I comment.
elb terraform internal autoscaling vpc
Sitemap 3
 Exactly one certificate is required if the protocol is HTTPS. First, we need to create the ALB itself. AWS NLBs and target groups do not support UDP, Global Accelerator does support UDP, but its expensive. If I'm wrong can I see an example of multiple routing rules pointing to different target groups? Detailed below. It allows us to write the wireframe of the cloud infrastructure we use by simple configuration language called HCL. elb on loadbalancing.tf line 25, in resource aws_lb_listener ecs_cluster_listener: Hostname. Required fields are marked *.
Exactly one certificate is required if the protocol is HTTPS. First, we need to create the ALB itself. AWS NLBs and target groups do not support UDP, Global Accelerator does support UDP, but its expensive. If I'm wrong can I see an example of multiple routing rules pointing to different target groups? Detailed below. It allows us to write the wireframe of the cloud infrastructure we use by simple configuration language called HCL. elb on loadbalancing.tf line 25, in resource aws_lb_listener ecs_cluster_listener: Hostname. Required fields are marked *.  The action with the lowest value for order is performed first. elb terraform Behavior if the user is not authenticated. ARN of the default SSL server certificate. A network load balancer (NLB) distributes IPv4 TCP/80 and TCP/443 traffic across two target groups of worker nodes with a healthy Ingress controller. Name of the SSL Policy for the listener. Max: 10. Today, Im going to show you how to construct the application load balancer in AWS with Terraform. Error: Unsupported block type elb asg Workers span the zones in a region to tolerate zone outages. If no other actions are matched, the default action will be taken. aws deployments alb downtime zero appoptics load Next, we can attach a listener to the ALB we have created.
The action with the lowest value for order is performed first. elb terraform Behavior if the user is not authenticated. ARN of the default SSL server certificate. A network load balancer (NLB) distributes IPv4 TCP/80 and TCP/443 traffic across two target groups of worker nodes with a healthy Ingress controller. Name of the SSL Policy for the listener. Max: 10. Today, Im going to show you how to construct the application load balancer in AWS with Terraform. Error: Unsupported block type elb asg Workers span the zones in a region to tolerate zone outages. If no other actions are matched, the default action will be taken. aws deployments alb downtime zero appoptics load Next, we can attach a listener to the ALB we have created.  A network load balancer (NLB) distributes IPv4 TCP/6443 traffic across a target group of controller nodes with a healthy kube-apiserver.
A network load balancer (NLB) distributes IPv4 TCP/6443 traffic across a target group of controller nodes with a healthy kube-apiserver.  Terraformer accelerates the Terraform migration process, How to add new policy to IAM role by Terraform, True Cause behind Additional Verification in ACM. Configuration block for an identity provider that is compliant with OpenID Connect (OIDC). #Bag of options to control resource's behavior. This component is not percent-encoded. This component is not percent-encoded. Add a custom route to the VPC route table.
Terraformer accelerates the Terraform migration process, How to add new policy to IAM role by Terraform, True Cause behind Additional Verification in ACM. Configuration block for an identity provider that is compliant with OpenID Connect (OIDC). #Bag of options to control resource's behavior. This component is not percent-encoded. This component is not percent-encoded. Add a custom route to the VPC route table. 
 Detailed below. All input properties are implicitly available as output properties. Can be set if protocol is TLS. elb ec2 asg aws balancing elb The alias record is output as ingress_dns_name for use in application DNS CNAME records. Thanks to that, we can safely modify the underlying infrastructure and quickly track the history of the change. The range is 1-604800 seconds (7 days). Defaults to #{host}. You do not have permission to delete messages in this group, Either email addresses are anonymous for this group or you need the view member email addresses permission to view the original message.
Detailed below. All input properties are implicitly available as output properties. Can be set if protocol is TLS. elb ec2 asg aws balancing elb The alias record is output as ingress_dns_name for use in application DNS CNAME records. Thanks to that, we can safely modify the underlying infrastructure and quickly track the history of the change. The range is 1-604800 seconds (7 days). Defaults to #{host}. You do not have permission to delete messages in this group, Either email addresses are anonymous for this group or you need the view member email addresses permission to view the original message.  To learn more about resource properties and how to use them, see Inputs and Outputs in the Architecture and Concepts docs. If you specify both forward block and target_group_arn attribute, you can specify only one target group using forward and it must be the same target group specified in target_group_arn.
To learn more about resource properties and how to use them, see Inputs and Outputs in the Architecture and Concepts docs. If you specify both forward block and target_group_arn attribute, you can specify only one target group using forward and it must be the same target group specified in target_group_arn.  A map of tags to assign to the resource.
A map of tags to assign to the resource.  Note that this listener has a default action. proxy alb nginx aws reverse signed behind self tls load which Additionally, the Listener resource produces the following output properties: The provider-assigned unique ID for this managed resource. "${aws_cognito_user_pool_client.client.id}", "${aws_cognito_user_pool_domain.domain.domain}", "https://example.com/authorization_endpoint". I didnt try on CodeDeploy.
Note that this listener has a default action. proxy alb nginx aws reverse signed behind self tls load which Additionally, the Listener resource produces the following output properties: The provider-assigned unique ID for this managed resource. "${aws_cognito_user_pool_client.client.id}", "${aws_cognito_user_pool_domain.domain.domain}", "https://example.com/authorization_endpoint". I didnt try on CodeDeploy.  In my case, I need to forward the traffic from AWS Application Load Balancer public interface to two different target groups. Finally, I found a solution to my case for my own. $ pulumi import aws:lb/listener:Listener front_end arn:aws:elasticloadbalancing:us-west-2:187416307283:listener/app/front-end-alb/8e4497da625e2d8a/9ab28ade35828f96. Note: aws.alb.Listener is known as aws.lb.Listener. This value is required for rules with multiple actions. Blocks of type target_group are not expected here.
In my case, I need to forward the traffic from AWS Application Load Balancer public interface to two different target groups. Finally, I found a solution to my case for my own. $ pulumi import aws:lb/listener:Listener front_end arn:aws:elasticloadbalancing:us-west-2:187416307283:listener/app/front-end-alb/8e4497da625e2d8a/9ab28ade35828f96. Note: aws.alb.Listener is known as aws.lb.Listener. This value is required for rules with multiple actions. Blocks of type target_group are not expected here.  listener configure externally nlb Detailed below. Valid values are between 1 and 50000. balancer elb balancers ec2 scaling fargate aws tracking target policy medium template cloudwatch stack attached launch sample using create Lastly, you can add your custom rules as you like with aws_lb_listener_rule. When I try a similar configuration, CodeDeploy complains that:
listener configure externally nlb Detailed below. Valid values are between 1 and 50000. balancer elb balancers ec2 scaling fargate aws tracking target policy medium template cloudwatch stack attached launch sample using create Lastly, you can add your custom rules as you like with aws_lb_listener_rule. When I try a similar configuration, CodeDeploy complains that:  Required if protocol is HTTPS or TLS. aws_lb resource will form the ALB as follows. The Listener resource accepts the following input properties: Configuration block for default actions. Detailed below. Provides a Load Balancer Listener Rule resource. Specify only when type is authenticate-oidc. Defaults to #{query}. Your email address will not be published. Listeners can be imported using their ARN, e.g.. ARN of the Target Group to which to route traffic.
Required if protocol is HTTPS or TLS. aws_lb resource will form the ALB as follows. The Listener resource accepts the following input properties: Configuration block for default actions. Detailed below. Provides a Load Balancer Listener Rule resource. Specify only when type is authenticate-oidc. Defaults to #{query}. Your email address will not be published. Listeners can be imported using their ARN, e.g.. ARN of the Target Group to which to route traffic.  Once the Terraform configuration is written, we can get the same resource by just applying it. The redirect is either permanent (HTTP_301) or temporary (HTTP_302). Maximum duration of the authentication session, in seconds.
Once the Terraform configuration is written, we can get the same resource by just applying it. The redirect is either permanent (HTTP_301) or temporary (HTTP_302). Maximum duration of the authentication session, in seconds.  Name of the Application-Layer Protocol Negotiation (ALPN) policy. Set of 1-5 target group blocks. Content type. Specify only if type is forward and you want to route to a single target group. A listener and target group may map different ports (e.g 3333 external, 30333 internal). To route to one or more target groups, use a forward block instead. This allows you to decouple the definition of the rules to a different project or different set of logic, and also matches the actual AWS API for these resources, which treats them as a separate resource. Type of routing action. practitioner cloud
Name of the Application-Layer Protocol Negotiation (ALPN) policy. Set of 1-5 target group blocks. Content type. Specify only if type is forward and you want to route to a single target group. A listener and target group may map different ports (e.g 3333 external, 30333 internal). To route to one or more target groups, use a forward block instead. This allows you to decouple the definition of the rules to a different project or different set of logic, and also matches the actual AWS API for these resources, which treats them as a separate resource. Type of routing action. practitioner cloud  Absolute path, starting with the leading "/". Add firewall rules to the worker security group.
Absolute path, starting with the leading "/". Add firewall rules to the worker security group. 

 Maybe something is changed on AWS or TF side and needs to be refactored. This action returns a 301 response with the redirection to the specific location by local.redirect_to. 25: target_group { All requests matching with the path /forward_to/* are routed to the target group this_tg. Detailed below. Protocol. Configuration block for target group stickiness for the rule.
Maybe something is changed on AWS or TF side and needs to be refactored. This action returns a 301 response with the redirection to the specific location by local.redirect_to. 25: target_group { All requests matching with the path /forward_to/* are routed to the target group this_tg. Detailed below. Protocol. Configuration block for target group stickiness for the rule.  Time period, in seconds, during which requests from a client should be routed to the same target group. Detailed below. Thanks David! Configuration block for using Amazon Cognito to authenticate users. balancer provisioning terraform application vpc assuming
Time period, in seconds, during which requests from a client should be routed to the same target group. Detailed below. Thanks David! Configuration block for using Amazon Cognito to authenticate users. balancer provisioning terraform application vpc assuming  Defaults to #{port}. That is what I did to prepare the load balancer running in front of our service. Get an existing Listener resources state with the given name, ID, and optional extra properties used to qualify the lookup. Query parameters, URL-encoded when necessary, but not percent-encoded.
Defaults to #{port}. That is what I did to prepare the load balancer running in front of our service. Get an existing Listener resources state with the given name, ID, and optional extra properties used to qualify the lookup. Query parameters, URL-encoded when necessary, but not percent-encoded.  The hashicorp language (HCL) not a hard language but the document is missing a lot of subjects and also there are some points in terraform are undocumented.Ive Google it before the make sure but Ive seen there is a lot of questions and issues about the Use more than one target group on AWS with terraform subject.I read the suggested solutions but they do not help me.
The hashicorp language (HCL) not a hard language but the document is missing a lot of subjects and also there are some points in terraform are undocumented.Ive Google it before the make sure but Ive seen there is a lot of questions and issues about the Use more than one target group on AWS with terraform subject.I read the suggested solutions but they do not help me.  The path can contain #{host}, #{path}, and #{port}. Set two different Target Groups on AWS Load Balancer with Terraform. Provides a Load Balancer Listener resource. The ELB could not be updated due to the following error: Green taskset target group cannot have non-zero weight prior to traffic shifting on listener arn:aws:elasticloadbalancing:.etc. Configuration block for creating an action that distributes requests among one or more target groups. Information for creating an action that returns a custom HTTP response. Valid values: deny, allow and authenticate. Save my name, email, and website in this browser for the next time I comment. elb terraform internal autoscaling vpc
The path can contain #{host}, #{path}, and #{port}. Set two different Target Groups on AWS Load Balancer with Terraform. Provides a Load Balancer Listener resource. The ELB could not be updated due to the following error: Green taskset target group cannot have non-zero weight prior to traffic shifting on listener arn:aws:elasticloadbalancing:.etc. Configuration block for creating an action that distributes requests among one or more target groups. Information for creating an action that returns a custom HTTP response. Valid values: deny, allow and authenticate. Save my name, email, and website in this browser for the next time I comment. elb terraform internal autoscaling vpc